- 31 Oct 2023
- 2 Minutes to read
- Print
- DarkLight
- PDF
Logz.io
- Updated on 31 Oct 2023
- 2 Minutes to read
- Print
- DarkLight
- PDF
AlertOps and Logz.io
Logz.io is a logging and tracing tool that generates application logs for use in performance monitoring or issue troubleshooting and allows customers to configure customizable alerts based on log query criteria.
AlertOps can be integrated with Logz.io to receive and respond to all alerts through a host of multichannel communication options. Based on the ruleset defined in your AlertOps Escalation Policy, incidents can be automatically opened and closed, depending on defined fields from incoming Logz.io data.
AlertOps' simple API/Webhook configuration can be used to integrate with Logz.io's monitoring, notification, and alerting capabilities.
AlertOps Inbound Integration Configuration
- From the main menu, click on Configuration and select Integrations from the submenu.
- In the Inbound Integration section, select API from the integration type dropdown menu.
- Click the +ADD API button.

- You will be redirected to a list of API integration templates. Select Logz.io from the list.
- To set up the integration, enter a name and select an Escalation Policy to guide escalations coming from this Integration, as well as recipient group(s) or recipient user(s).
- Click the Submit button to save.
- Copy the integration webhook URL for use in the next steps.
Once the integration has been saved, you can use the Advanced Settings to define various configurations for alerts to be received and processed. For example, you can define when to open and close alerts based on the payload obtained from Logz.io.
Logz.io Integration Configuration
To setup an outbound call to AlertOps for alert management you need to set up a Notification Endpoint in Logz.io:
- In your Logz.io portal, in the left navigation pane, under 'Traces', select 'Notification Endpoints'
- Select '+ Add Endpoint'
- Select Endpoint Type as 'Custom', give a name, method type as 'POST' and for URL, paste the inbound integration URL which you obtained from AlertOps.
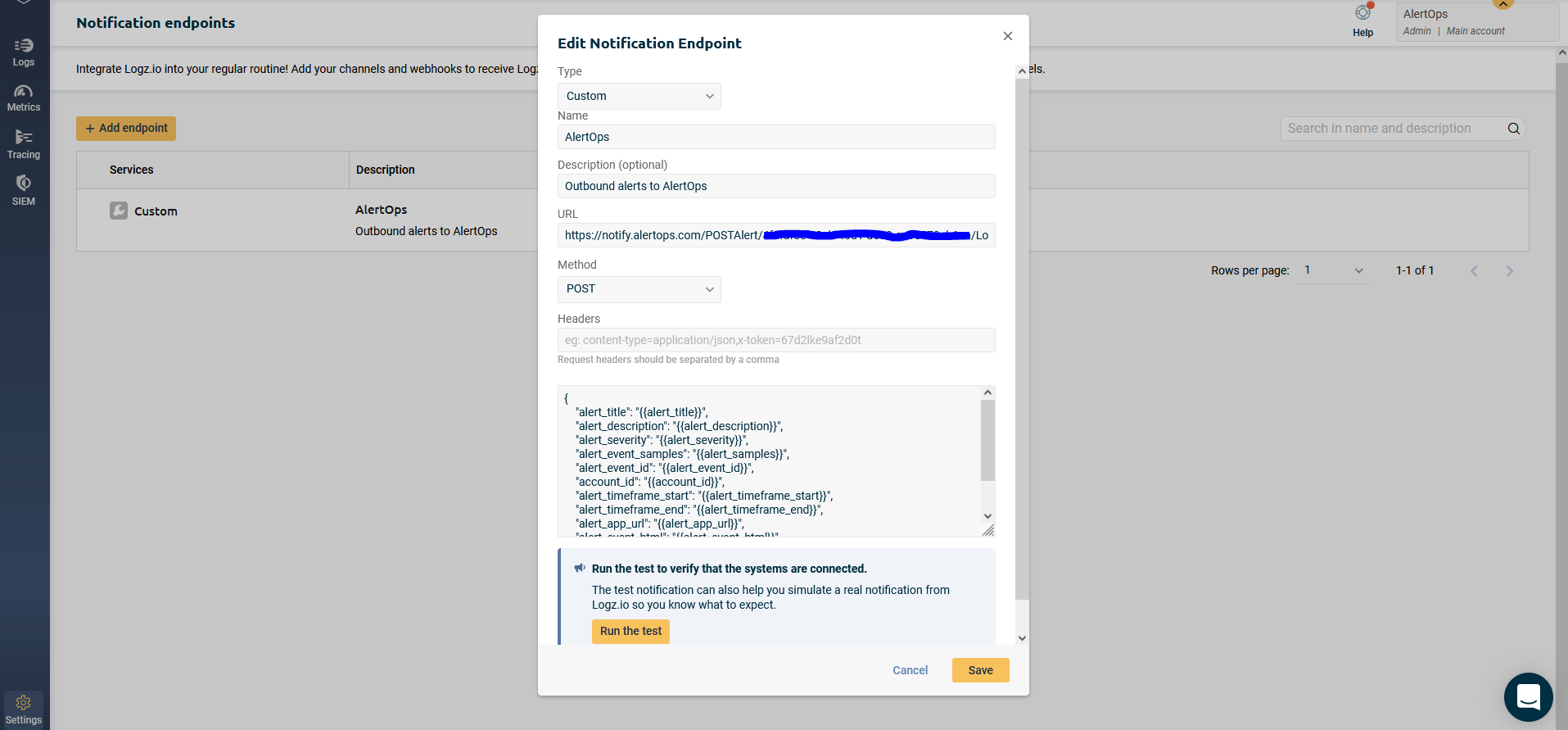
- For payload body, paste the following JSON body in the text field provided:
{ "alert_title": "{{alert_title}}", "alert_description": "{{alert_description}}", "alert_severity": "{{alert_severity}}", "alert_event_id": "{{alert_event_id}}", "account_id": "{{account_id}}", "alert_timeframe_start": "{{alert_timeframe_start}}", "alert_timeframe_end": "{{alert_timeframe_end}}", "alert_app_url": "{{alert_app_url}}", "alert_event_html": "{{alert_event_html}}", "alert_definition_id": "{{alert_definition_id}}"}
- You can run a test to make sure alerts are sent out to AlertOps.
- Save the endpoint.
- Configure the Alert itself to include the Notification Endpoint we just created under the 'Notify' step (for Logs/Metrics you configure). You can also add the AlertOps endpoint from here.
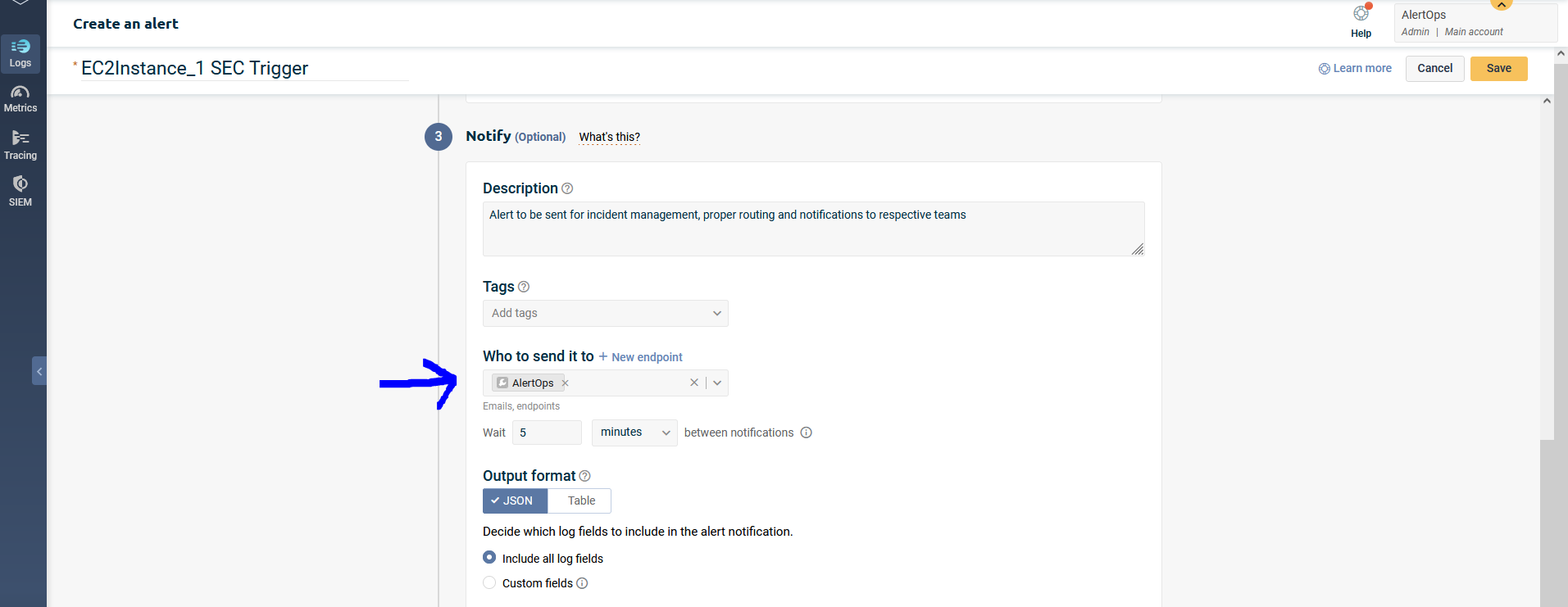
You have now configured a notification endpoint and associated alerts with this endpoint. Any trigger event in your Logz.io environment will send an alert to AlertOps.
Message logs, alert specific information can be viewed in the “Inbound Log” section in AlertOps Dashboard. Alerts can be viewed in the ‘Alerts’ tab as well.
Alert Triggering Information:
AlertOps will automatically create an incident when a new alert is received from Logz.io when the alert_severity field contains "SEVERE" or "HIGH".
If an alert with the status "SEVERE" or "HIGH" matches an existing Open Alert, AlertOps will recognize the new alert as a duplicate and ignore the alert.
The alert will be recorded in the Inbound Messages table as “Mapped Appended.”
AlertOps will automatically close the same incident when an alert with alert_severity contains 'LOW' or 'INFO'.
References


