- 02 Dec 2025
- 1 Minute to read
- Print
- DarkLight
- PDF
PRTG
- Updated on 02 Dec 2025
- 1 Minute to read
- Print
- DarkLight
- PDF
PRTG Integration Guide
PRTG Network Monitor is the all-in-one monitoring solution that collects and displays status information from your IT infrastructure. Integrate AlertOps’ alert management platform with PRTG to receive and respond to critical alerts through email, SMS, push notification, and phone alerts. AlertOps ensures that alerts received from PRTG always reach the correct, available team member by utilizing escalation policies and on-call schedules.
AlertOps Configuration
- From the main menu, click on Integrations and then select Inbound Integrations from the sub menu.
- Select API tab
- Select the 'ADD API INTEGRATION' button, you should now be on the API Integration Detail page. Select PRTG from the pre-built Integration Templates.
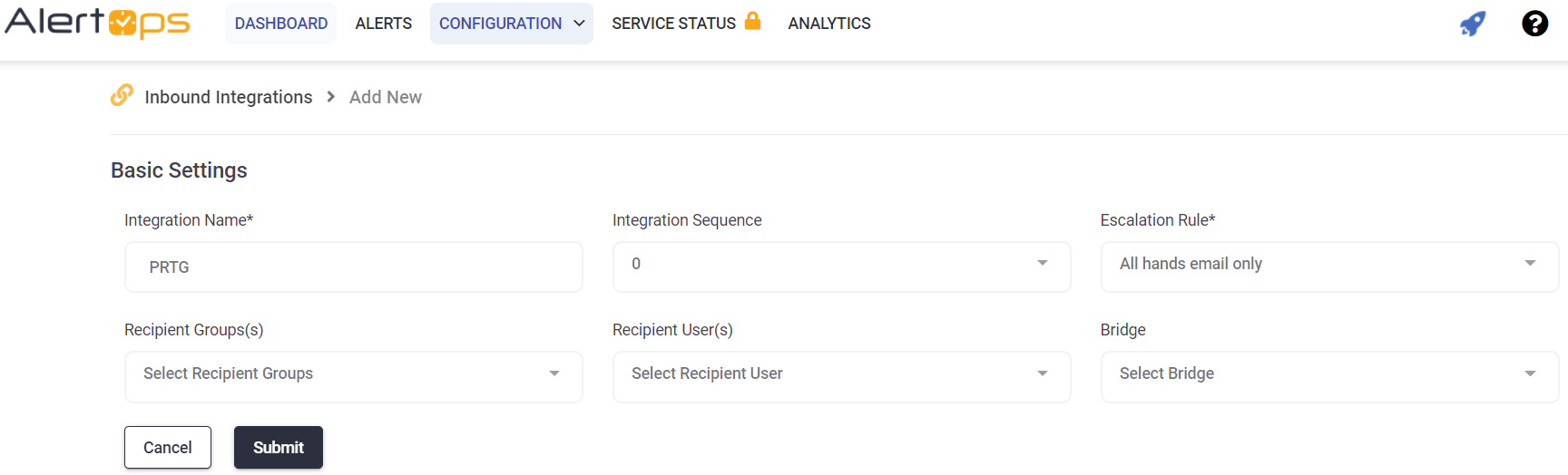
- Enter a name for the integration.
- Select an escalation rule to determine the integration's escalation policy.
- Enter the names of recipient group(s) and recipient user(s).
- Click 'SAVE.' then, click 'COPY URL' to copy the URL endpoint to be used in the PRTG configuration.
PRTG Network Monitor Configuration
Step 1: In the PRTG Network Monitor menu option Select Setup -> Account Settings -> Notification Templates
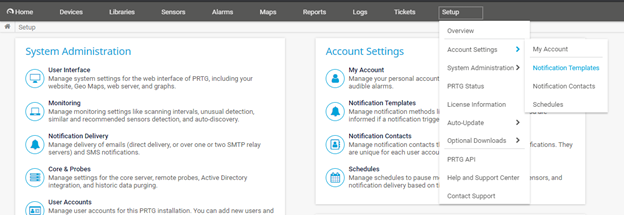
Step 2: Select Add Notification Template
Step 3: Select “Execute HTTP Action”
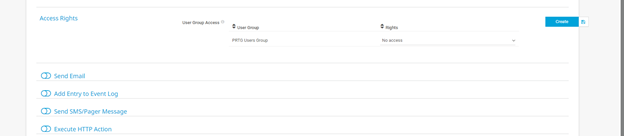
Step 4: Configure your HTTP Action with your AlertOps Integration Endpoint URL and the HTTP Method as POST. For the Notification Summarization select "Always notify ASAP never summarize"

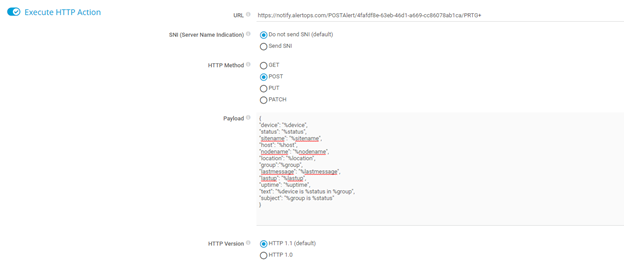
Step 5: Configure Notification Payload with the following JSON below
{
"device": "%device",
"status": "%status",
"sitename": "%sitename",
"host": "%host",
"nodename": "%nodename",
"location": "%location",
"group":"%group",
"lastmessage": "%lastmessage",
"lastup": "%lastup",
"uptime": "%uptime",
"text": "%device is %status in %group",
"subject": "%group is %status"
}Step 6: Define triggers for group or device using the notification you created above.
Alert Triggering Information
AlertOps will automatically create an incident when a new alert is received from PRTG with an IncidentStatus status of “Down.”
If an alert with status “Down” matches an existing Open Alert, AlertOps will recognize the new alert as a duplicate and ignore the alert. The alert will be recorded in the Inbound Messages table as “Mapped Appended.”
AlertOps will automatically close the same incident when an alert with an IncidentStatus status “Up” is received.
Testing and Troubleshooting
Click here to read about Web API Testing and Troubleshooting.


