- 16 Jan 2024
- 3 Minutes to read
- Print
- DarkLight
- PDF
Azure Monitor
- Updated on 16 Jan 2024
- 3 Minutes to read
- Print
- DarkLight
- PDF
AlertOps and Azure Monitor
AlertOps’ alert management system can be integrated with Azure Monitor to receive and respond to (predefined status mappings) alerts/notifications through email, SMS, push notification or phone alerts. AlertOps would ensure that the alert would reach the appropriate team by using proper workflows, escalation policies and schedules. Based on your ruleset, incidents can be automatically opened and closed, depending on what the monitor alerts on.
The above scenario and scope for integration is due to the fact that AlertOps has a very flexible and simple API/Webhook configuration feature that can be leveraged with Azure's monitoring, connecting, notifications/alerting capabilities.
AlertOps Inbound Integration
You can define an inbound integration in AlertOps to receive the event/alert information from the Webhook that you will define. The next section will show you how to create a webhook alert to send out notifications.
AlertOps would ensure based on these notifications received, that it would always reach out and assign to the correct person/team by utilizing its escalation policies, schedules, and workflow features. AlertOps provides Inbound Integrations to integrate with numerous monitoring, chat and ITSM tools.
At a high level this is how the flow looks like, you define an API integration in the AlertOps platform by defining settings like Integration Name, Escalation rules, recipient users/groups. Once an integration is defined, a unique API URL is generated. This acts as webhook or the gateway through which events from Azure Alerts reach AlertOps and thus an incident/alert is created correspondingly. The API can be defined with various settings like URL mappings, filters, escalations etc. as required. You will have to create a webhook action group in Azure Alerts to send event information.
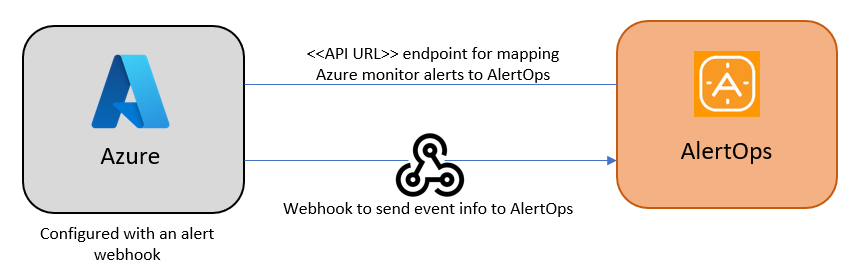
Configure Inbound Integration in AlertOps
- Under 'Configuration' select 'Integrations'. From the Inbound Integration section, select 'API' from the dropdown and then click the 'Add API' button.
- Select Azure Monitor from the list of available integration options.
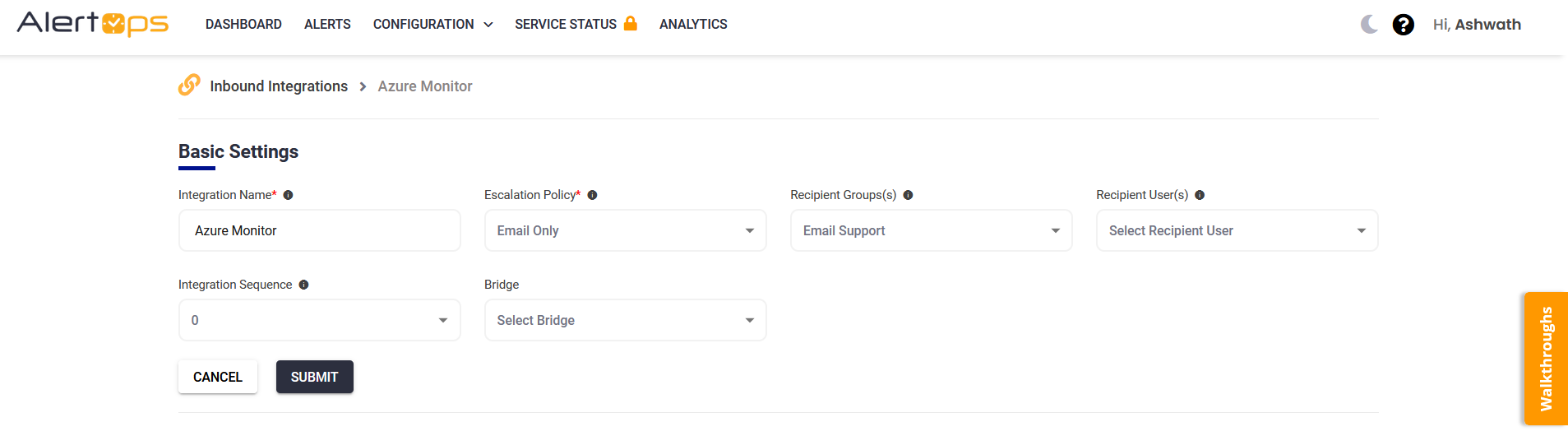
- Once you select the integration, you can then specify basic settings like the integration name, escalation policy, names of the recipients/groups for which the alerts must be assigned to.
- Once you click save, the API Integration will be created, and you will be given a unique URL which acts as the access point and needs to be configured at the source (in this case the webhook in Azure Monitor), to send events. You can find the integration you just created, and you can give advanced settings and define various configurations for the alerts to be received and processed. For example, you can define when to open and close alerts based on the response obtained from the API call, filters for the incoming JSON payload etc.
5. AlertOps will open an alert when the ‘data^essentials^monitorCondition’ field from the JSON payload received (mapped to Source Status field), contains 'Fired'. You can similarly define URL mappings as you want, owing to the flexibility provided by AlertOps’ Open API integrations. You can provide other filters and match with regex as well. You can also test the generated URL.
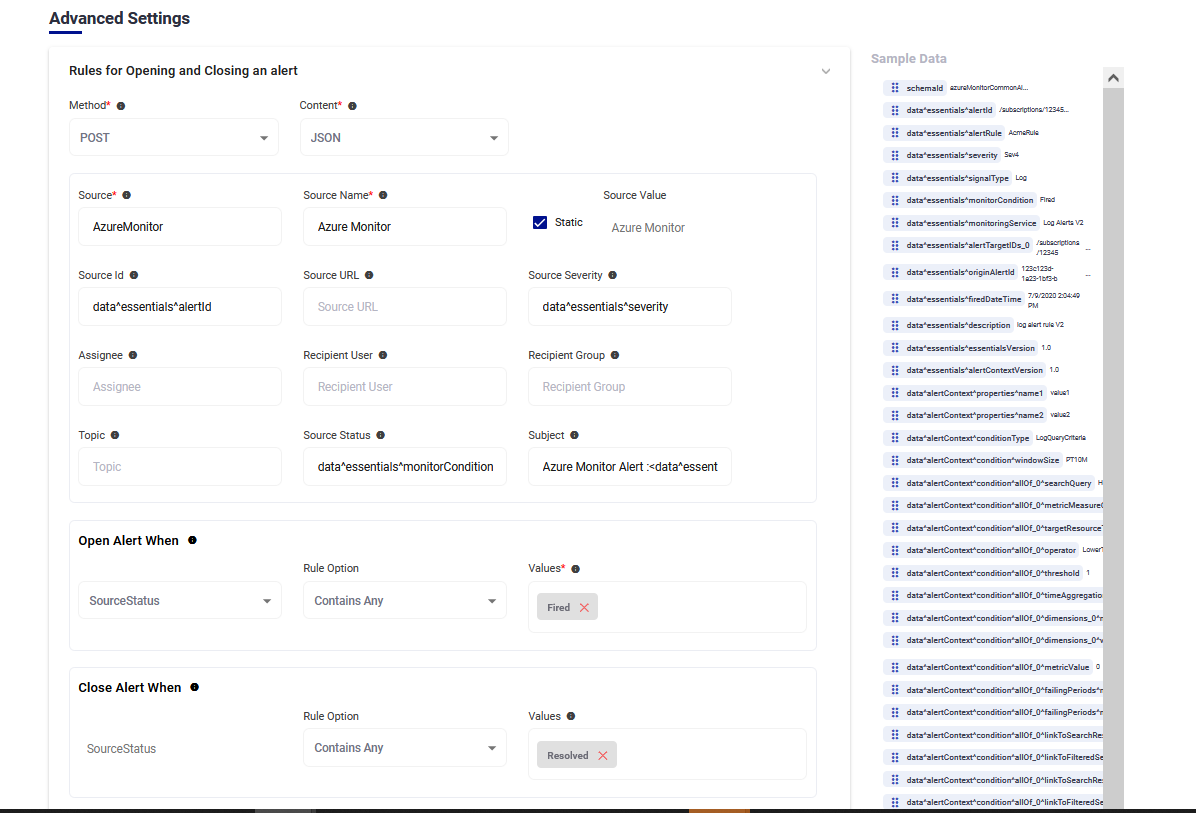
The Sample Data/payload is mapped to the fields for the common alert payload generated by Azure Monitor. It is entirely up to the user to determine, based on the payload sent from Azure to map accordingly. AlertOps provides you with the flexibility to map incoming information in any way possible. For more information on the payloads sent out by Azure Monitor take a look at,
https://learn.microsoft.com/en-us/azure/azure-monitor/alerts/alerts-common-schema
Configure the Integration in Azure Monitor
In Azure Monitor, you would have to create an Action group and associate it with an alert rule for any resource/service.
1) In your Azure environment/portal, go to your specific resource/service
2) Go to the 'Monitor' section, and then select 'Alerts'
3) Under 'Action Groups', click on 'Create' > go to the 'Actions' tab
4) Select 'Action Type' as Webhook, paste the AlertOps Inbound Integration API URL.
5) Select 'Yes' to 'Enable the Common Alert Schema'
6) Save. Ensure that the Webhook action group you created is associated with your corresponding Alert Rule.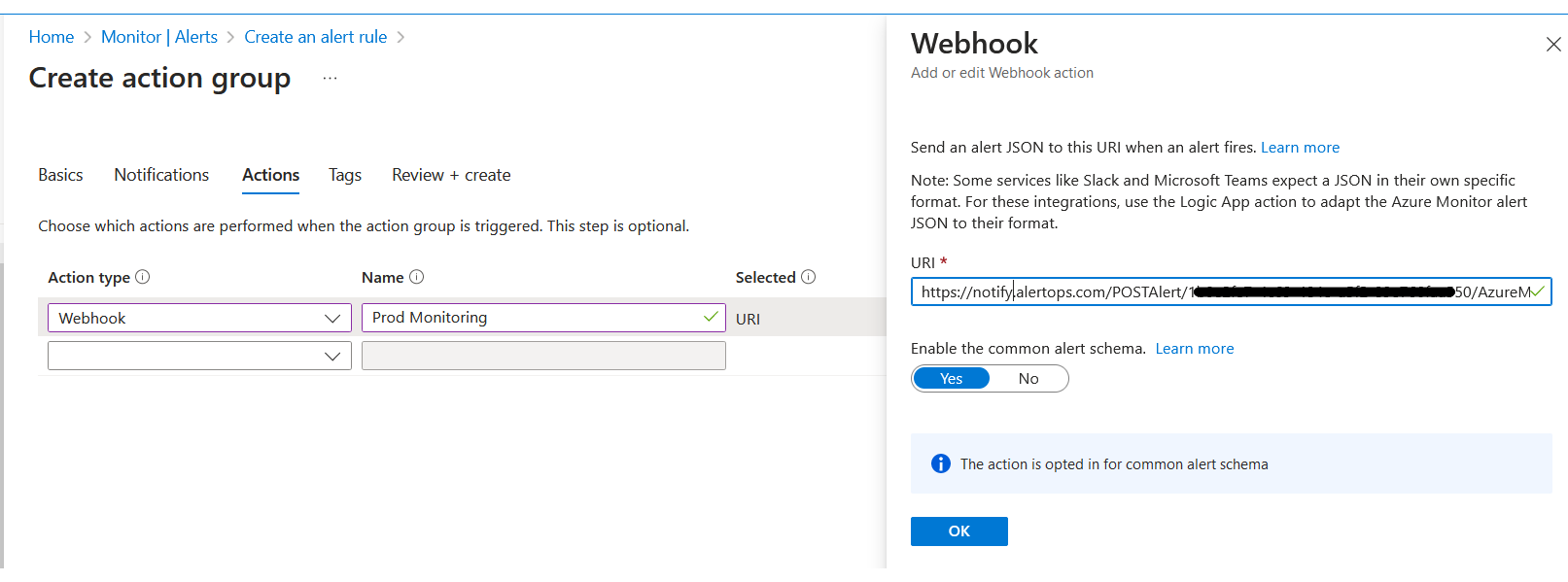
Thats it! You have defined an Action Group and associated it with an Alert Rule, that will send out JSON payload for the monitor information.
You can view the payload/information in the “Inbound Log” (or ‘Alerts’ tab) in AlertOps.
Alert Triggering Information
AlertOps will automatically create an incident when a new alert is received from Azure Monitor when the data^essentials^monitorCondition status field contains “Fired”.
If an alert with statuses “Fired” matches an existing Open Alert, AlertOps will recognize the new alert as a duplicate and ignore the alert. The alert will be recorded in the Inbound Messages table as “Mapped Appended.”
AlertOps will automatically close the same incident when an alert with a data^essentials^monitorCondition status contains “Resolved”.
References
Azure Monitor Alert JSON Schemas


